Streamline and Simplify Multifactor Authentication


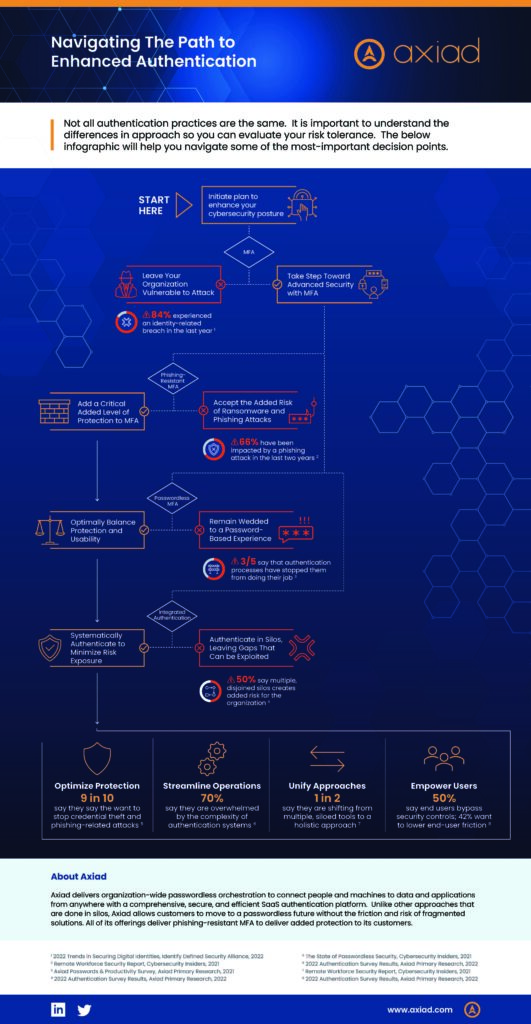
A Holistic Approach to Authentication
Integrated Authentication Solutions
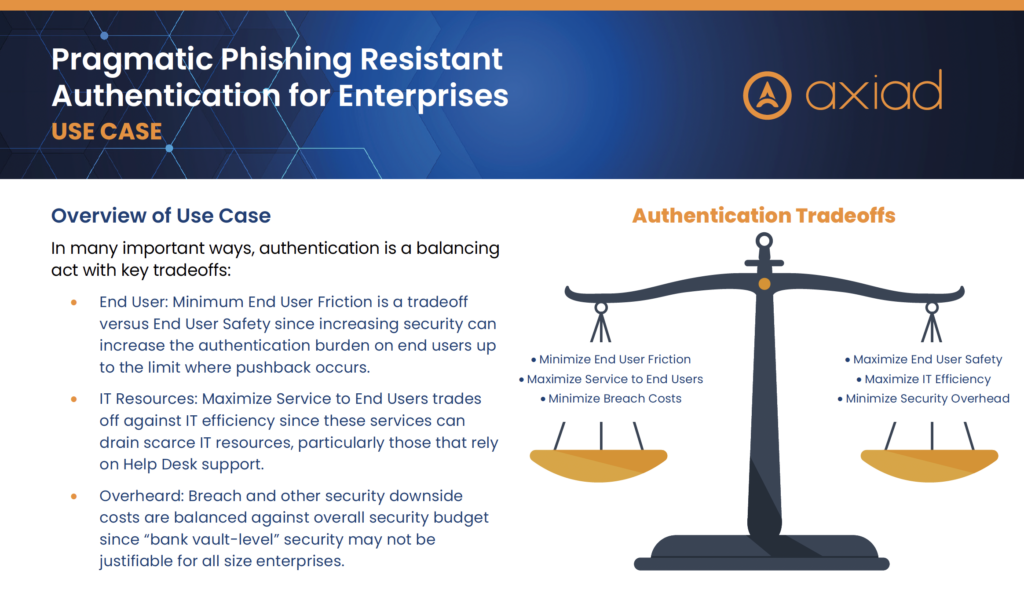
Attain phishing-resistant authentication
Protect privileged access users
Secure access for decentralized users
Enable digital signatures and encryption
Make passwordless invisible
Leverage PKI as a service
Deliver a publicly trusted CA
Manage a full-certificate lifecycle
Secure your DevOps teams
Extend your machine identity platform
Secure your workstations
Streamline your YubiKey deployment
Protect your Windows environment
Add cloud PKI to your Microsoft Azure AD
Make your IAM solution passwordless
Remove the need for the helpdesk
Administer with a single pane of glass
Simplify authentication infrastructures
Stop security breakdowns during M&A
Implement a Zero Trust strategy
Address regulatory requirements
Adhere to White House OMB guidance
Deliver compliance and audit reporting
Reduce the cost of cyber insurance
-
Protect Your Workforce
Attain phishing-resistant authentication
Protect privileged access users
Secure access for decentralized users
Enable digital signatures and encryption
Make passwordless invisible
-
Secure Your Machine Identities
Leverage PKI as a service
Deliver a publicly trusted CA
Manage a full-certificate lifecycle
Secure your DevOps teams
Extend your machine identity platform
-
Supplement Existing Environments
Secure your workstations
Streamline your YubiKey deployment
Protect your Windows environment
Add cloud PKI to your Microsoft Azure AD
Make your IAM solution passwordless
-
Satisfy Regulations and Mandates
Address regulatory requirements
Adhere to White House OMB guidance
Deliver compliance and audit reporting
Reduce the cost of cyber insurance
-
Empower Your Organization
Remove the need for the helpdesk
Administer with a single pane of glass
Simplify authentication infrastructures
Stop security breakdowns during M&A
Implement a Zero Trust strategy
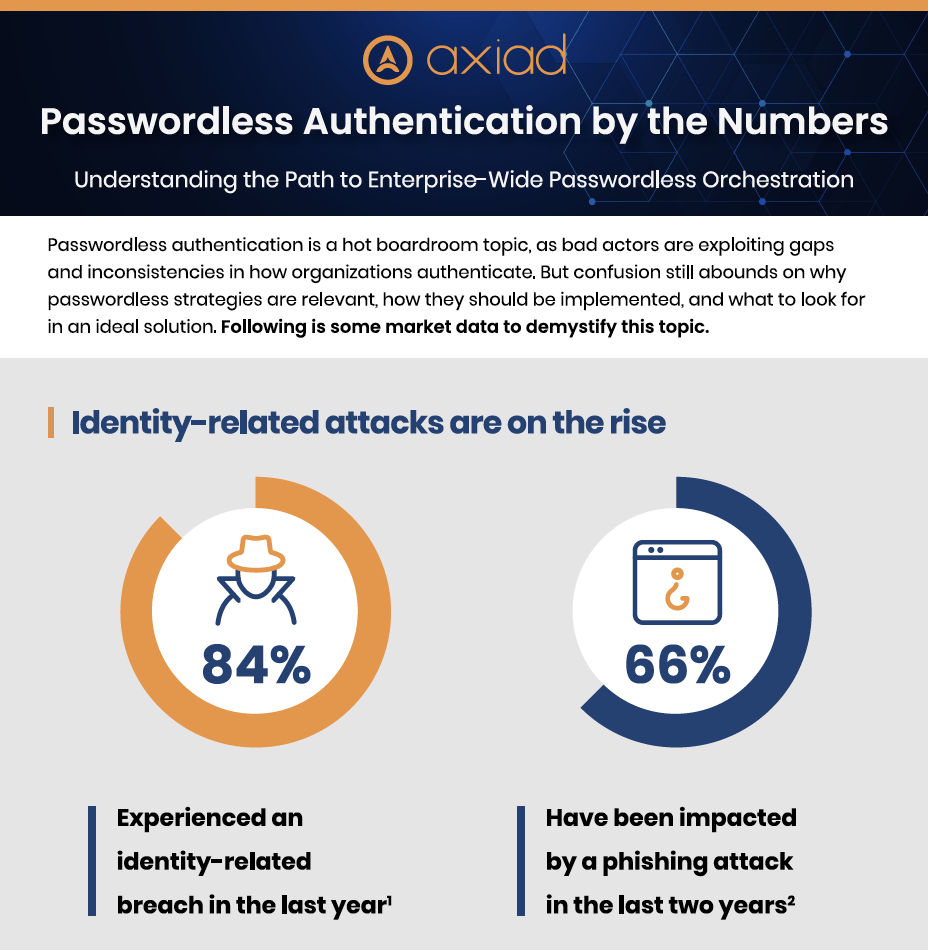
Cybersecurity Trends
CyberEdge’s Annual Cyberthreat Defense Report (CDR)


Trusted and Proven
-
6.9×Average ROI delivered to customers
-
<3Average months to pay back investment
-
9.6Average rating (of 10) on PeerSpot
-
99.9%End user availability for Axiad Cloud
Authentication Done Differently
-
Complete: Leverage a single platform for all your people & machine authentication needs, regardless of underlying IT complexity
-
Simple: Empower end users with high levels of orchestration so they can easily access what they need, when they need it
-
Secure: Retain maximum control over credentials, with no commingled keys, to minimize vulnerabilities
-
Resilient: Build a foundation for your IAM strategy that can easily adapt as your requirements evolve
World-Class Customers

Explore Related Resources